Security
The security landscape has changed.
Are your sights on the right target?


Cloud Security
Quickly discover, identify and remediate cloud risks to keep your business secure. Identify, prioritize, and remediate security risks and compliance issues across your cloud estate spanning AWS, Azure, Alibaba Cloud, Google Cloud and Kubernetes.
Email Security
- Cloud Email Security
- AI Based platform
- Behavioral Learning
Identity and context awareness enables Abnormal to stop all types of email attacks, from business email compromise to account takeovers to supply chain fraud and more.

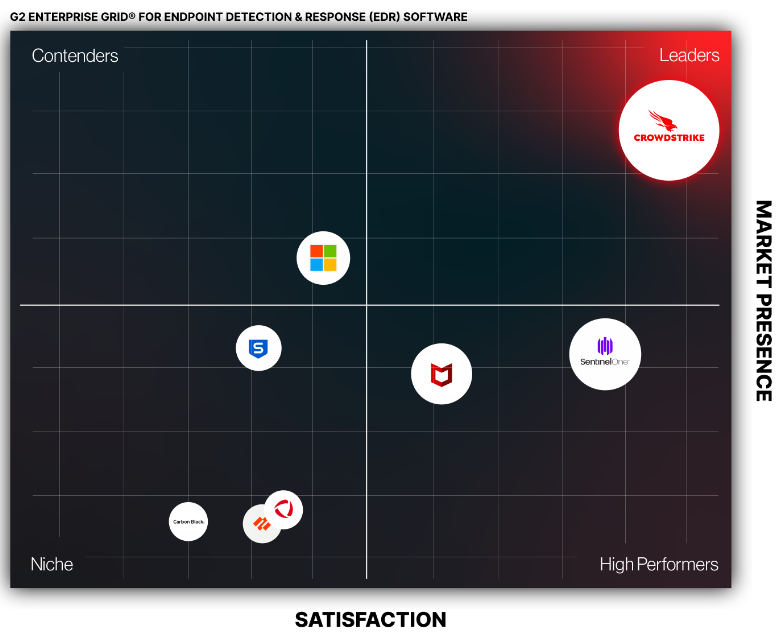
Threat Detection.
One Platform. One Agent.
Comprehensive visibility and protection across your critical areas of risk: endpoints, workloads, data, and identity.
- Endpoint Security (EDR / XDR)
- Cloud Security
- Threat Intelligence
- Identity Protection
- Security & IT Ops
Perimeter Protection
There is still a critical need for firewalling and basic perimeter protection. We can help with these foundational aspects of security.
- Firewalls
- SD-WAN
- Remote Access
If your desire is to enable a Zero Trust model, we have security offerings to help build that structure in your environment.
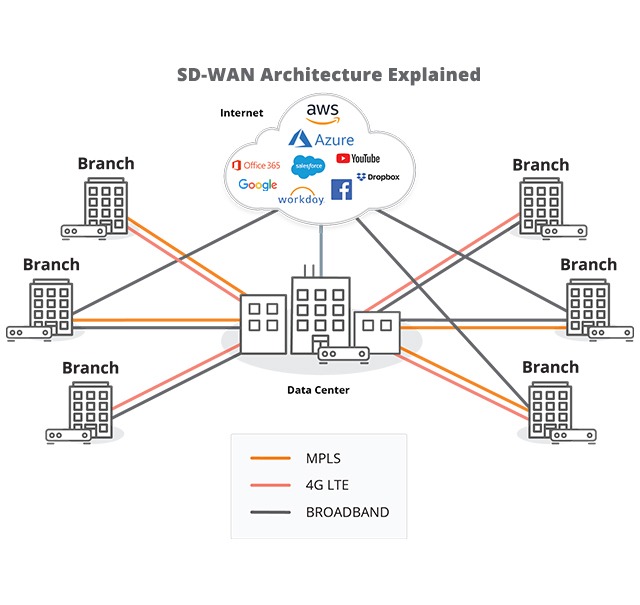
SD-WAN
Firewall , malware protection, and URL filtering in the network, delivering security and application performance under a single management pane.
- Managed SD-WAN
- Remote VPNaaS (Private Access)
- Multi-Cloud Connectivity
SD-WAN – leveraging the power of the Cloud – is global, easily adjustable, and infinitely configurable. Think of it: being able to see, control and optimize your entire network allows you to:
- Prioritize traffic based on your business priorities
- Replace local hardware, and in particular, the corporate edge router, which age out quickly and require constant, local maintenance. Some SD-WAN solutions even have WIFI access capabilities, making it an ideal solution for a remote office or retail chain
- Evaluate network traffic patterns and choose the most efficient and reliable routes across the network in real time